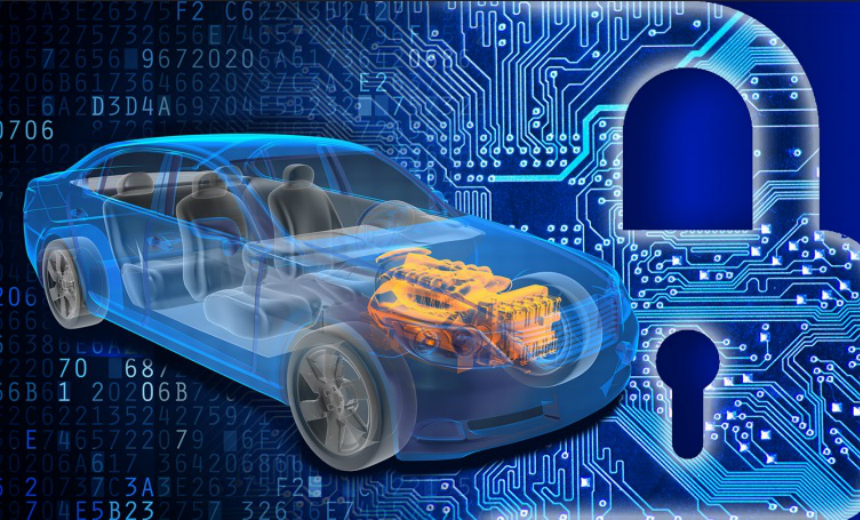
Up to fifty distinct automotive IoT devices (computers) are vulnerable to cyberattacks in today’s autos. This is why cybersecurity in the automotive industry is so important.
In today’s vehicles, there can be dozens of computers doing various tasks, such as navigation and entertainment. Steering, braking, and the engine are only some of the systems that are monitored and controlled by computers. This highlights the importance of automobile cyber security.
A lack of security in a vehicle’s electronic systems leaves it vulnerable to theft of data. It’s important for customers, automakers, and original equipment manufacturers to worry about cyber security in the automotive industry.
But how much do you really know about cyber security for cars? We will discuss the major dangers to automotive IoT and connected vehicles. We will also get into the specifics of what cybersecurity means in the automotive sector.
The Critical Importance of Cybersecurity in the Automotive Industry
We’ve already established that computers play a crucial role in the management of many aspects of today’s automobiles. Hackers can take information, such as your location via GPS, from a car whose technology isn’t secure.
But it gets much worse: hackers can provide commands, thereby replacing the driver with unwitting robots. Even more alarming than having your information taken is the possibility that a hacker could take control of your vehicle. The steering, brakes, and engine can all be controlled by remote controls, and the air conditioner and windshield wipers can be turned on and off.
Strategies for Cyber Attacks on Automobiles
Then, what steps must a potential hijacker take to assume command of a moving vehicle or its associated systems? They need to figure out how to gain access to the car’s computer systems first. As a result, they’ll be able to gain access to an automobile’s electronic control unit (ECU; this is the industry term for a computer or other IoT device used in the automotive sector) and look for a vulnerable feature.
Khan pointed up a few potential weak spots in our defenses against cyber attacks:
Attacks with one’s own body as a weapon.
For example, if a car is in the shop getting repaired or if someone breaks into it, that person now has direct physical access to the vehicle and can launch an attack. The networks, ports, and connectors found within a vehicle are routinely exploited in these sorts of assaults. During use, an attacker could have installed hardware or software to take control of your car.
Physical weaknesses that are not immediately apparent.
This form of attack, unlike the first, necessitates the use of a medium. Firmware upgrades, SD cards, USB drives, etc., are all examples of the various channels that can be used. If an attacker can convince a car’s owner to put in a compromised MP3 player, for instance, they have gained access to the vehicle’s network.
The security holes in wireless networks. Wi-Fi and Bluetooth assaults are examples of the former, while GPS and cellular technology are examples of the latter. A hacker doesn’t need to gain access to your vehicle in order to launch one of these assaults.
It is possible to trick sensors.
While there have been no confirmed incidents of this nature, Khan warns that this does not indicate that sensors cannot be compromised.
Unless you have some sort of internal defense in place, a hacker who gains access to your car’s virtual interior is free to cause as much damage as they like.
To prevent hackers from accessing vehicle systems and to stop them from wreaking havoc once inside, robust automotive cybersecurity is essential.